WSO Per-app VPN Demos (Internal Domain Access)
- airwatchhk

- Jan 3, 2022
- 2 min read
Updated: Sep 6, 2022
Remote work is now a new standard. Employees are expecting to work from anywhere.
Per-app VPN tunnel can allow remote employees to get access to internal domains. This is like getting a behind firewall enterprise resources mobilized. As the name implies, per-app VPN is a secure connection between app and enterprise resource. It is not a full device VPN. With this, we can provide a more granular control on traffic rerouting. Only enterprise traffic is routed through per-app VPN. Other traffic like open internet browsing traffic is not routed through VPN server. This makes the solution more scalable.

Security is always a top priority when opening internal enterprise resources.
first of all, data is encrypted end to end:

In addition, WSO UAG VPN only accepts certificate based identification. A certificate with both user ID and device ID is presented for dual authentication.
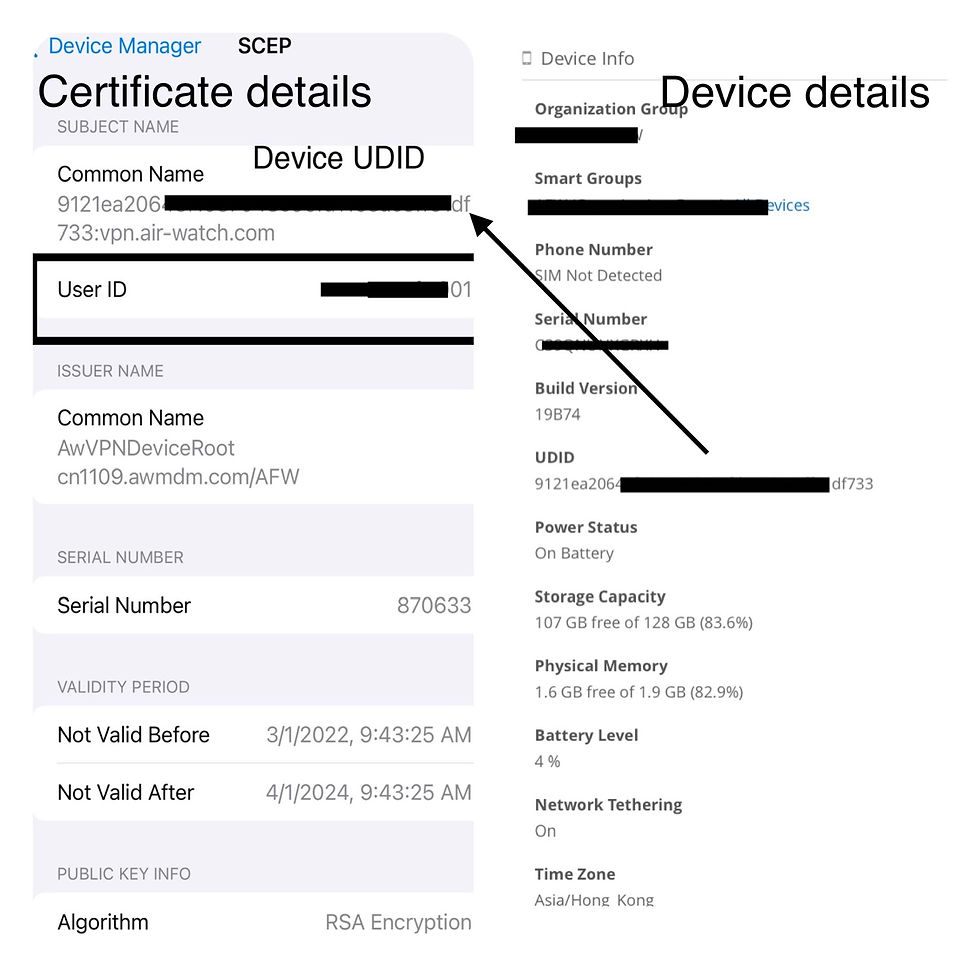
Only authenticated user using a compliant device is allowed to access behind firewall website with an authorized app.
This is a zero trust security model. No implicit trust and every stage of interaction is continuously validated.
A user must pass all the following verifications to get access green light.
1. User ID authentication
2. Device compliance
3. App authorization
4. Enterprise web resource authorization
User ID and device compliance check are enforced by VPN profile installed by WSO UEM. In case a device is out of compliance or a user right is revoked, VPN access will be taken away immediately.
App and web resource authorization are defined by device traffic rules which is enforced by client tunnel app.
Let‘s now look at the DTR configuration. There are four options to choose from. In this demo, tunnel is selected.

Look at the following setting, the two internal domains are resolved by VPN server.
By design, when DTR (Device Traffic Rule) is “tunnel”, DNS resolution is performed by VPN server.

In the Windows 10 demo video, per the DTR rule, Chrome browser traffic to the internal domains will be tunneled. This is how we can enforce application and web resource authorization.
Please note that this works not only on web browser but also on any other applications.
In case you need to look at the VPN client log for troubleshooting

iOS demo
It is setup in a way that Safari browser will access internal domain (my.euc852.local) through VPN server.
I have the tunnel log opened up in this demo so you can see that internal domain is resolved by the tunnel server. The phone was connected from outside of the domain so it was not capable to get a internal domain resolved.

The VPN profile was optional so it can be installed and removed without going to the console.

User can manage the profile by login to self service portal. With this setup, we can do a demo all an iPhone. This makes demo much more easy and portable.

Demo video:
In case you need to get your Device Traffic Rules modified, please add a new version to your VPN profile to make sure VPN profile on device is refreshed.




Comments