Demo of WSO UEM + Azure AD Device Compliance Integration
- airwatchhk

- Dec 10, 2021
- 4 min read
Updated: Feb 13, 2025
To use this feature, you will need to have AAD P1 and Intune E3 license ready. This is to my best knowledge. Please make sure you verify the latest license requirements with the subject matter expert.

The integration involves Azure side setup and UEM side setup.
1. On Azure AD, add WSO UEM as a partner compliance. Please note that you will need to add iOS once and Android once. The UI does not support multiple device selection.
2. Copy the Azure AD tenant ID and paste it to UEM directory services setup page to get UEM and Azure AD integrated. Please note that you will need to have WSO Intelligence enabled before doing this step. On UEM console, go to monitor -> Intelligence and “opt in“.

You now knew the two main steps to get the integration completed. Let’s go to the Azure console and start the configuration.
Start by enabling Workspace ONE partner compliance on Azure side. To be exact, it is the Microsoft Endpoint Manager admin console you have to login to.
Goto "Tenant administration" -> "Connectors and tokens" -> "Partner compliance management"

By design, device type is added one by one. If you want to have both iOS and Android enabled, you will need to do “Add compliance partner” twice.
Sample screen to add a device type.

You are now done with Microsoft endpoint management side setup. Let’s move to Azure AD console.
To enable Azure AD compliance on UEM, we need the Azure AD tenant ID. It is also known as Directory ID. You can look it up from the Azure AD properties.

Copy the tenant ID. Now we can jump to WSO UEM console.
On UEM console -> Directory Services, have Azure AD enabled, fill in the Directory ID (AKA tenant ID) you copied before,
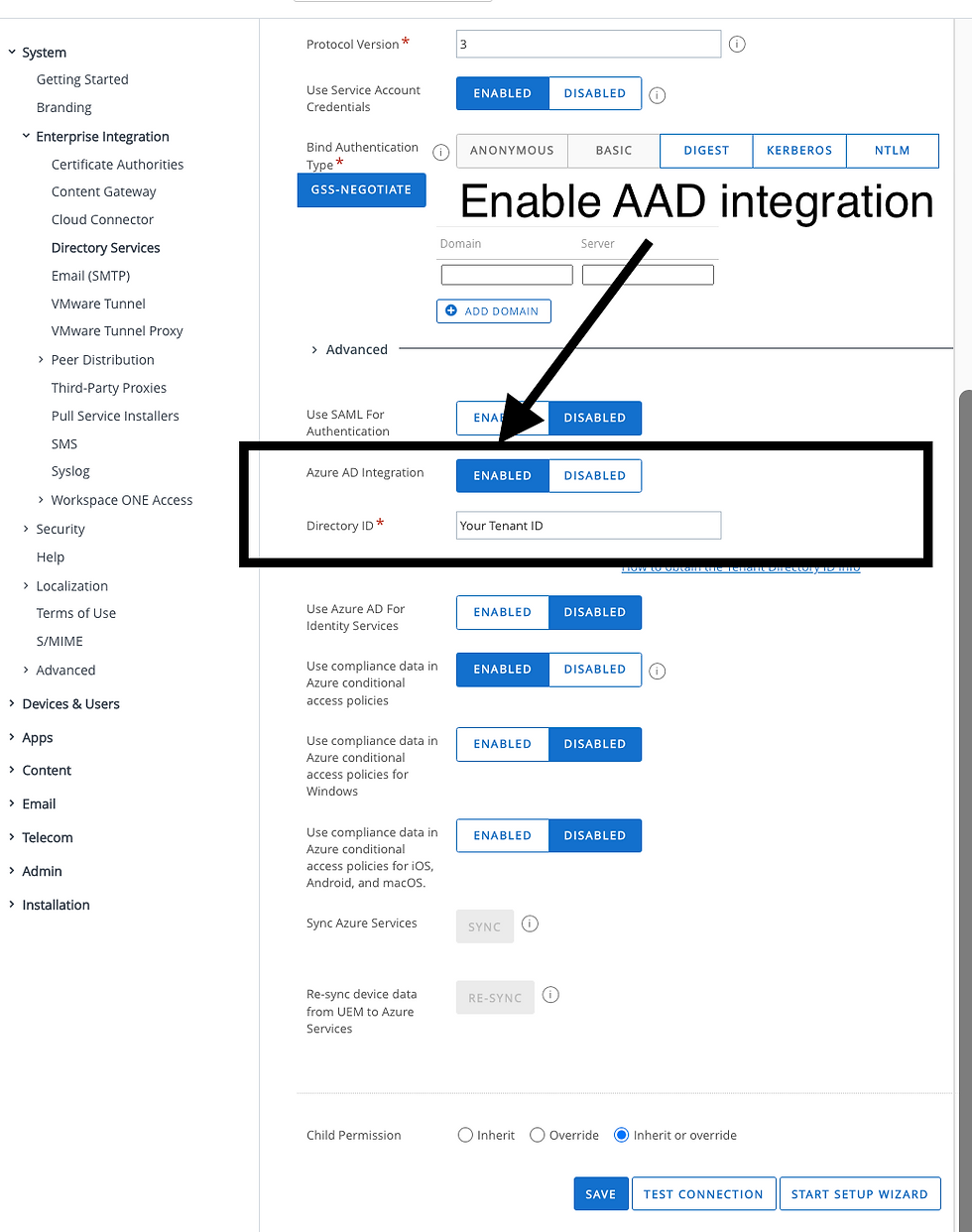
enable “Use Compliance data……”

Once the integration is done, you will see WSO conditional access added to Azure Enterprise applications list on Azure console. https://portal.azure.com
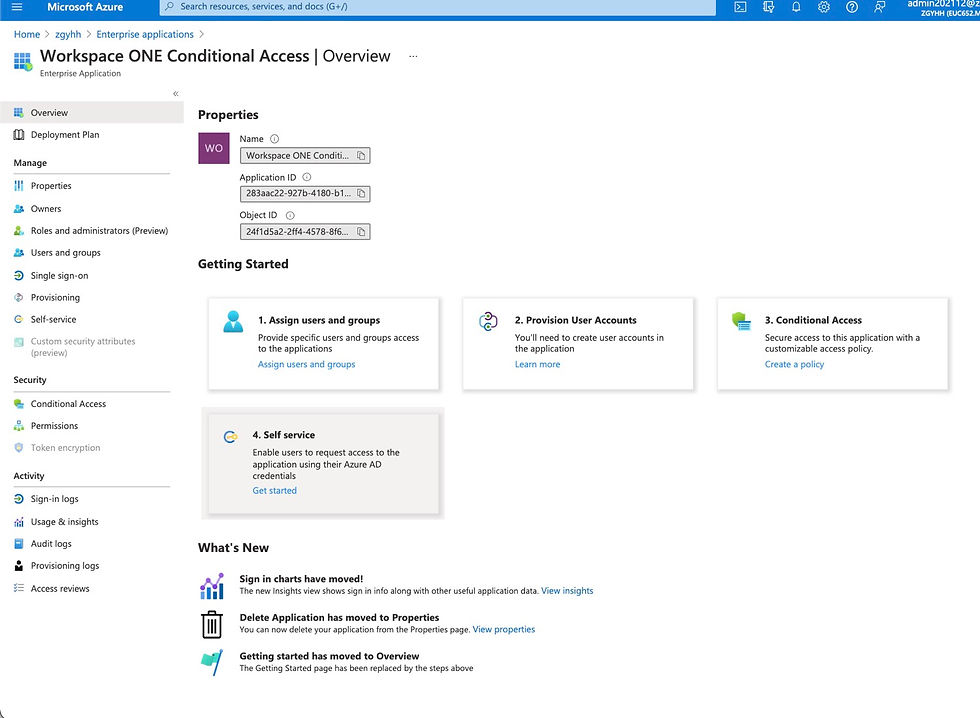
It is a good idea to check if required permissions are granted. There are six of them. If any of them is not granted, please go ahead and grant the missing permission.

Also make sure to assign the app to your user

On UEM console, make sure you have HUB services enabled so Web links can be deployed to a device. We need user to click on a web link to get his device registered to the Azure AD.

With HUB catalog enabled, Web links are published to HUB service catalog. We have to get one link created for Android and one for iOS.
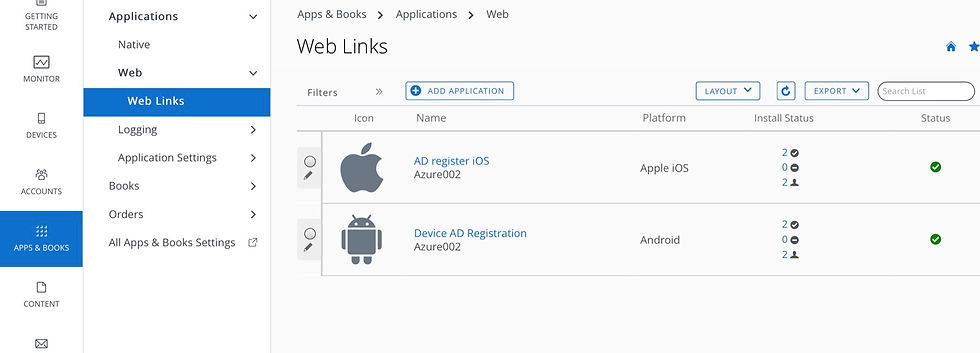
Please see the link addresses below.

When user click on a link, WSO HUB agent will be waken up and HUB agent will invoke Microsoft Authenticator to get a device registered to Azure. Authenticator will return a registered device ID to HUB agent. This is how UEM gets to identify a registered device when it feeds compliance status to Azure.
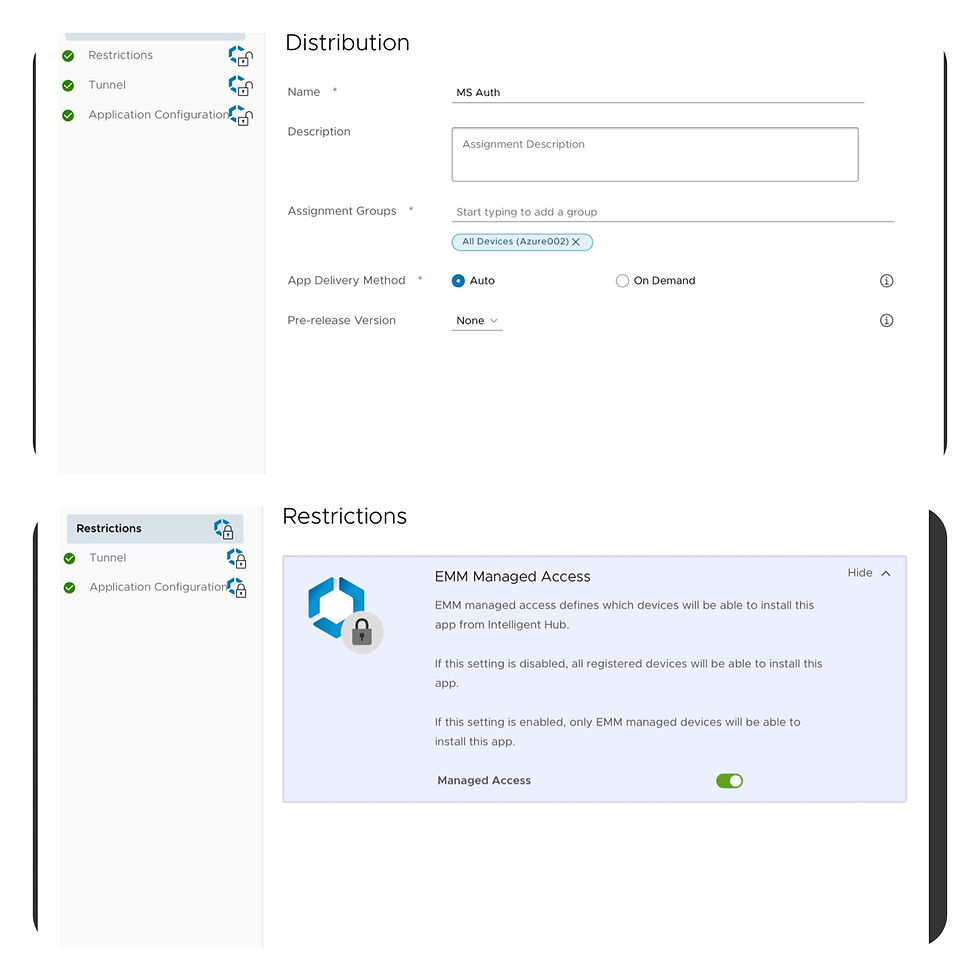
Don‘t forget to have the Authenticator app published to your app catalog. Make them managed and auto pushed.

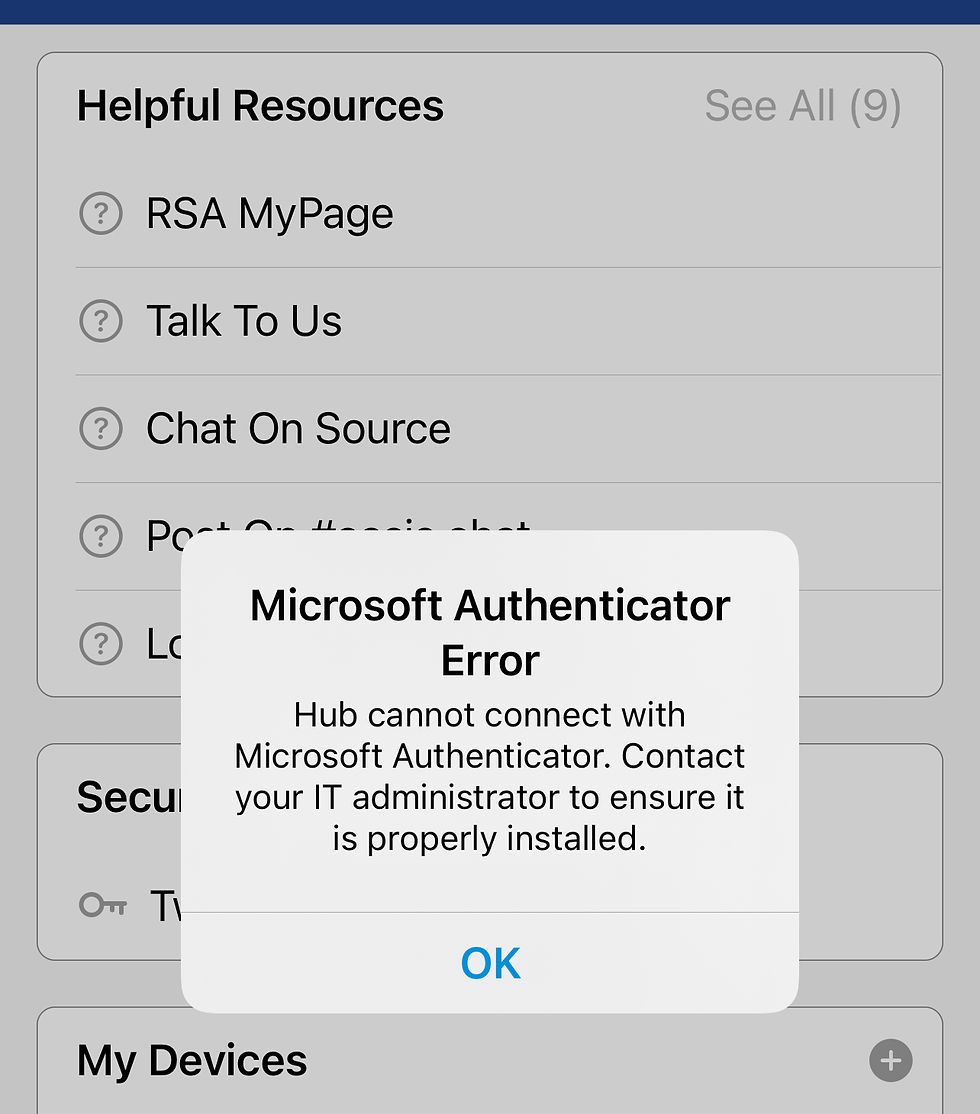
If Authentucator is not managed, user will end up seeing this error when WSO HUB tries to connect to Authenticetor for device registration to Azure AD.
This is a video showing the error.
We can now grab a device and get it enrolled into WSO as usual.
After enrollment is done, open HUB agent and go to HUB catalog, click on a device registration link we published above.
Enrolled devices are now on both WSO UEM and Azure AD. Compliance status on Azure is fed from WSO after a device is registered on Azure AD.
WSO console

Azure Console

Please watch the below demo videos on how user get his device registers to Azure AD. The compliance status is fed from UEM via Intelligence in no time.
iOS demo video
Android demo video
An alternative to check the device MDM and compliance is through MS company portal app. Sign in as the device owner to see device information.

If compliance status is still missing, you can initiate a manual data synchronization on UEM console.

You will need to get conditional access policy on Azure AD setup to enforce device compliance. Here is sample conditional access policy you can configure on AAD.
On Azure AD Conditional Access

create conditional access policy to only allow access to compliant devices

Choose the resources you want to protect. Be careful not to include all apps to lock out everything.

The device compliance control on device is enforced by the Authenticator. On iOS, you can use SSO extension to allow other non MSAL apps to get access to protected resources.
Please refer this for details on how to get it working with iOS Boxer and native email client or any other app leveraging SafariViewController for modern authentication.
The is a sample SSO extension profile to allow Boxer to connect with a registered and compliant iOS device.

This is a demo video showing Boxer is allowed to authenticate after device is registered and marked as compliant. You can see that Boxer was blocked until the device was registered and marked as compliant.
In case the compliance status is not updated,

check if Microsoft intune and AAD P1 license has been assigned to users.

important note:
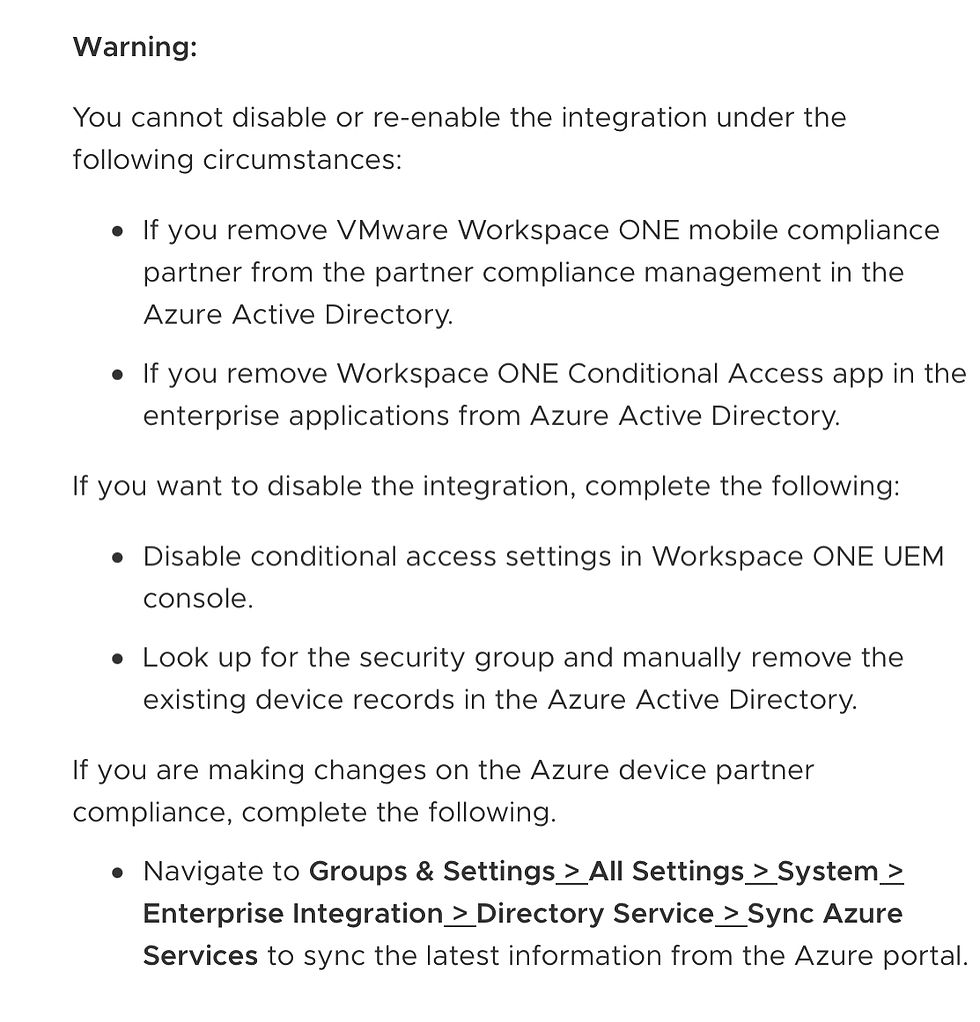
If you have the right license but not seeing status update, you can check both the UEM log and Azure log.
On UEM, you can see in the conditional access logs that it send out the event, at least to the service running in Intelligence.
and in the audit logs of Azure it would show a successful update log entry.
More details on getting WSO + Azure AD compliance setup:
You are now ready to create a conditional access policy based on device compliance status.
References:



Comments