Setting up Mobile SSO for WSO Access [2/3] - Android
- airwatchhk

- Dec 13, 2021
- 2 min read
Updated: Sep 24, 2022
Let’s start with how Android Mobile SSO works. iOS Mobile SSO is Kerberos based while Android is Per-app VPN tunnel based. Having said that, all you need to have is VPN tunnel app on Android. You don’t need to have your own UAG if you don’t already have one yet. So, how is the traffic routed to Access? We do it by device traffic rules (DTR). Whitelisted apps and their traffic to Access defined in DTR is routed through a SaaS certificate proxy server.
In this demo, I have had DTR setup to get Access: “aw-azure004.vmwareidentity.asia“ traffic from “WSO“ and “Chrome“ proxy through “certproxy.vmwareidentity.asia:5262”
** Make sure it is “certproxy“, not “cert-proxy”. If you had “cert-proxy” in your configuration, please change it to “certproxy”.
Here is the route:
Chrome/WSO -> certificate proxy -> Access

We can now look at how to get ”Mobile SSO” working on Android. If you have not had “Mobile SSO” configured before, please jump to my other blog post https://airwatchhk.wixsite.com/euc852/post/setting-up-ios-mobile-sso-for-wso-access for things like Access integration, HUB service setup, UEM basic account synchronization and Mobile SSO setup wizard before you continue here.
Mobile SSO wizard will get a VPN profile generated for legacy Android.

Because I wanted to get Mobile SSO setup for Android for Enterprise, I simply got the legacy profile replicated to an AFE profile. The AFE profile is optional so it can be removed and added to demonstrate conditional access.

The two profiles are exactly the same in content. Please note that the VPN server defined in the profile is non-existent dummy host generated by the wizard.


Chrome is the app used in my testing. I have had Chrome posted to my HUB catalog and marked it as a VPN app. It is assigned with the AFE VPN profile I got replicated from the system generated legacy VPN profile.
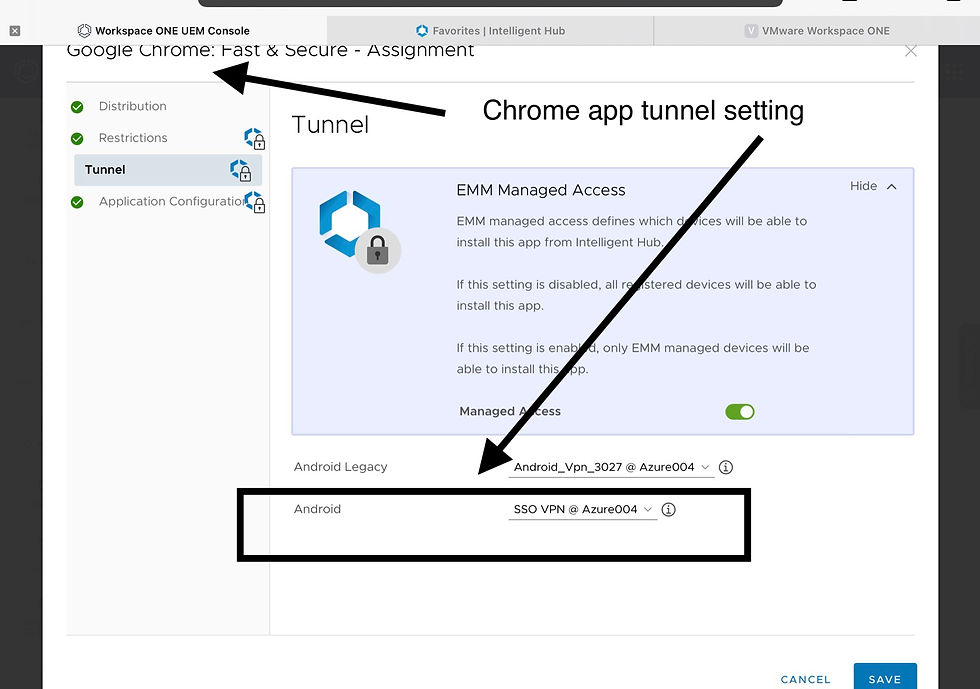
Tunnel app is also required to help to execute the DTR. You can also use the tunnel app to tell if a VPN profile is applied. Without an VPN profile, the app will prompt a message to ask you to contact your IT administrator.

I also got two web links published. They simply made navigation between sites easier.

Let’s jump to Access side. All configurations should be generated automatically.
In Authentication method, Mobile SSO (for Android) is enabled.

Click the pencil icon to edit Mobile SSO (for Android). To get Access to trust the certificate from VPN, we will have to export the client root certificate from UEM and to import it into Access.

In the Built-in Identity Provider, please make sure 1, 2 and 3 are all checked.

The next thing to check is policy. Make sure Mobile SSO is assigned to Android with no fallback. With this setup, only managed Android with VPN profile is allowed to access.

This is the audit log when a device is logging in successfully using Mobile SSO.

This is an audit log when a device is blocked without Mobile SSO.

Demo video on Android Mobile SSO with an Android device enrolled in work profile mode. In the video, you will see that I can get optional VPN profile added and removed from the profile manager.

Reference: https://youtu.be/F4-kZMd9Cls
![Setting up Mobile SSO for WSO Access [3/3] - Windows 10](https://static.wixstatic.com/media/798605_edc748606add452c849ef0b03eb6315b~mv2.png/v1/fill/w_728,h_410,al_c,q_85,enc_avif,quality_auto/798605_edc748606add452c849ef0b03eb6315b~mv2.png)
![Setting up Mobile SSO for WSO Access [1/3] - iOS](https://static.wixstatic.com/media/798605_6428905fd2e04a069771c705c95405eb~mv2.png/v1/fill/w_980,h_735,al_c,q_90,usm_0.66_1.00_0.01,enc_avif,quality_auto/798605_6428905fd2e04a069771c705c95405eb~mv2.png)
Comments